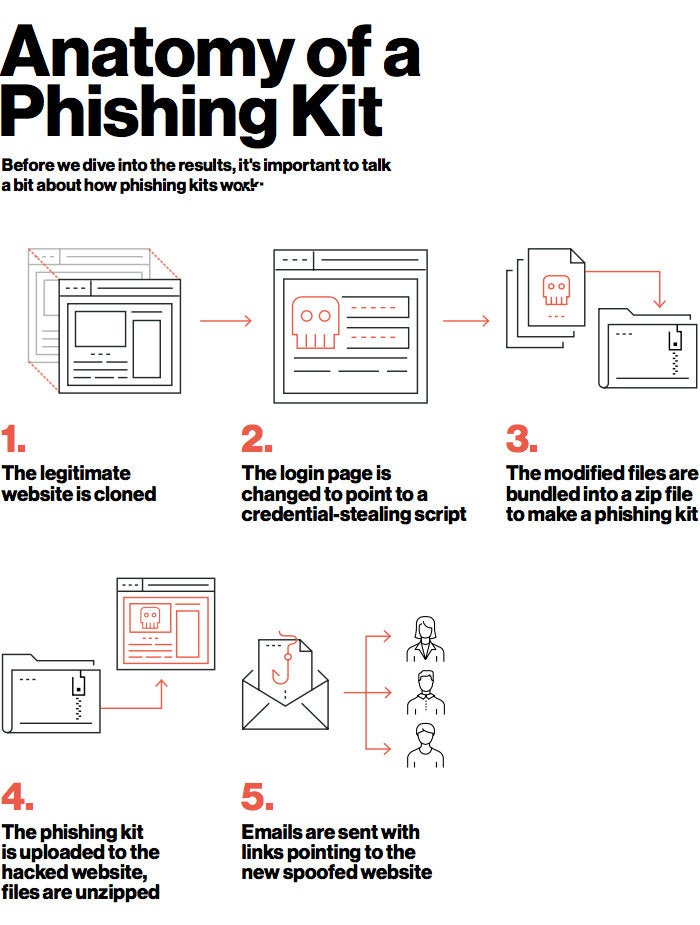
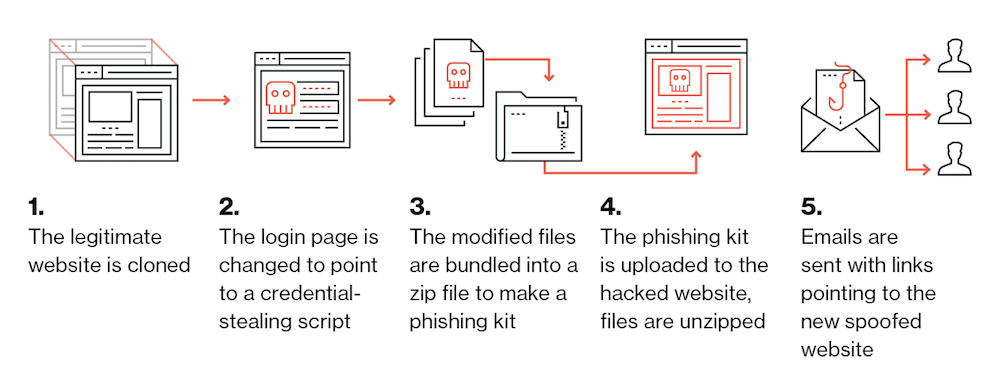
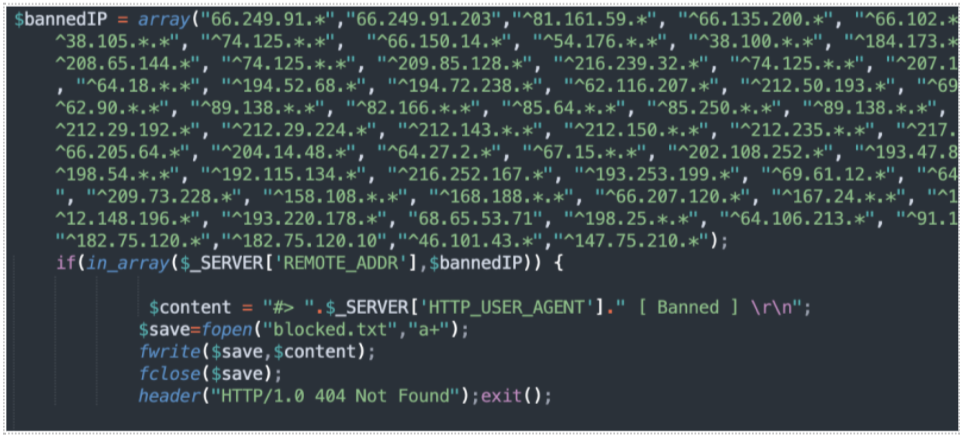
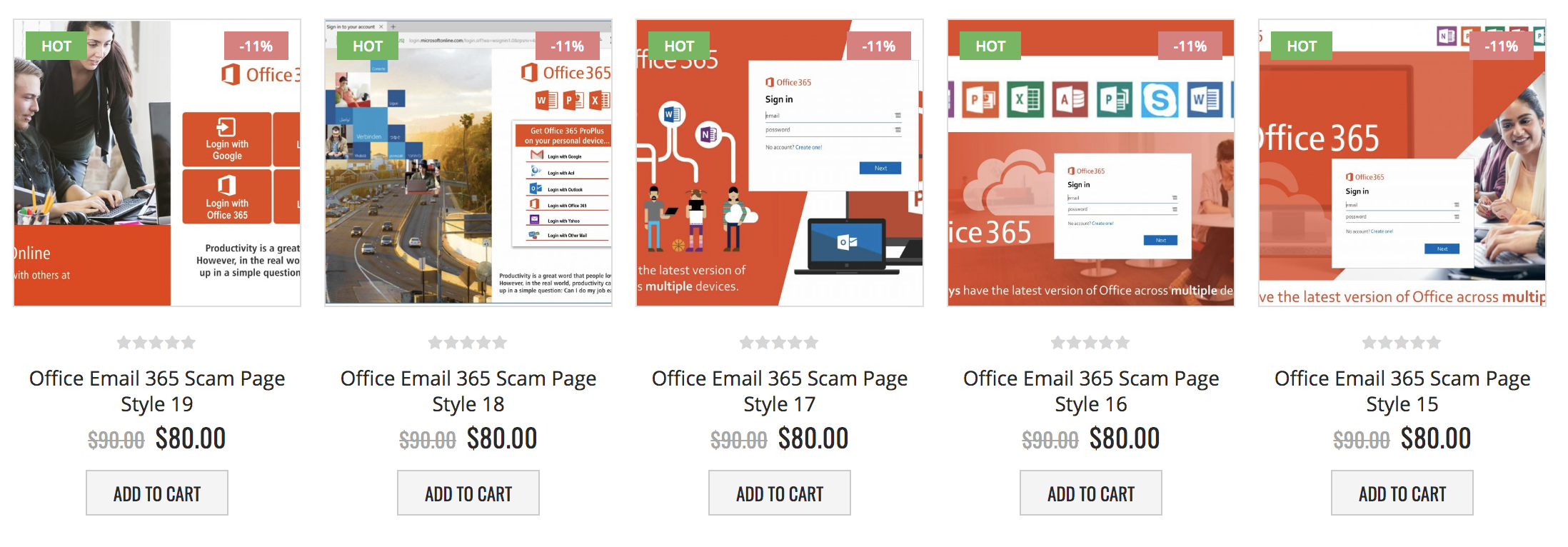
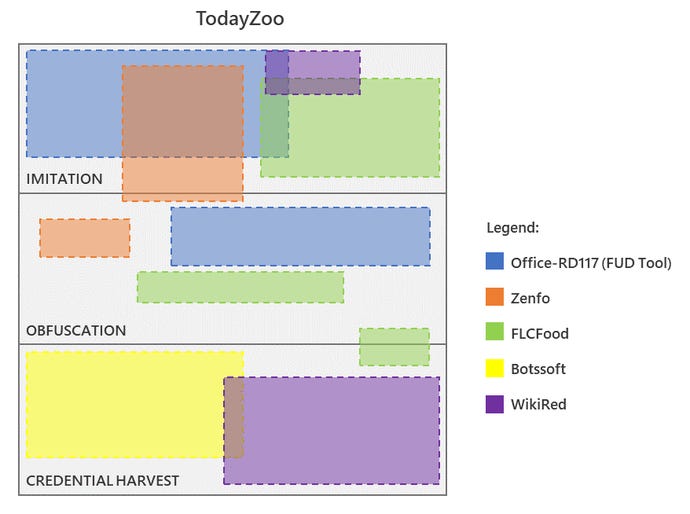
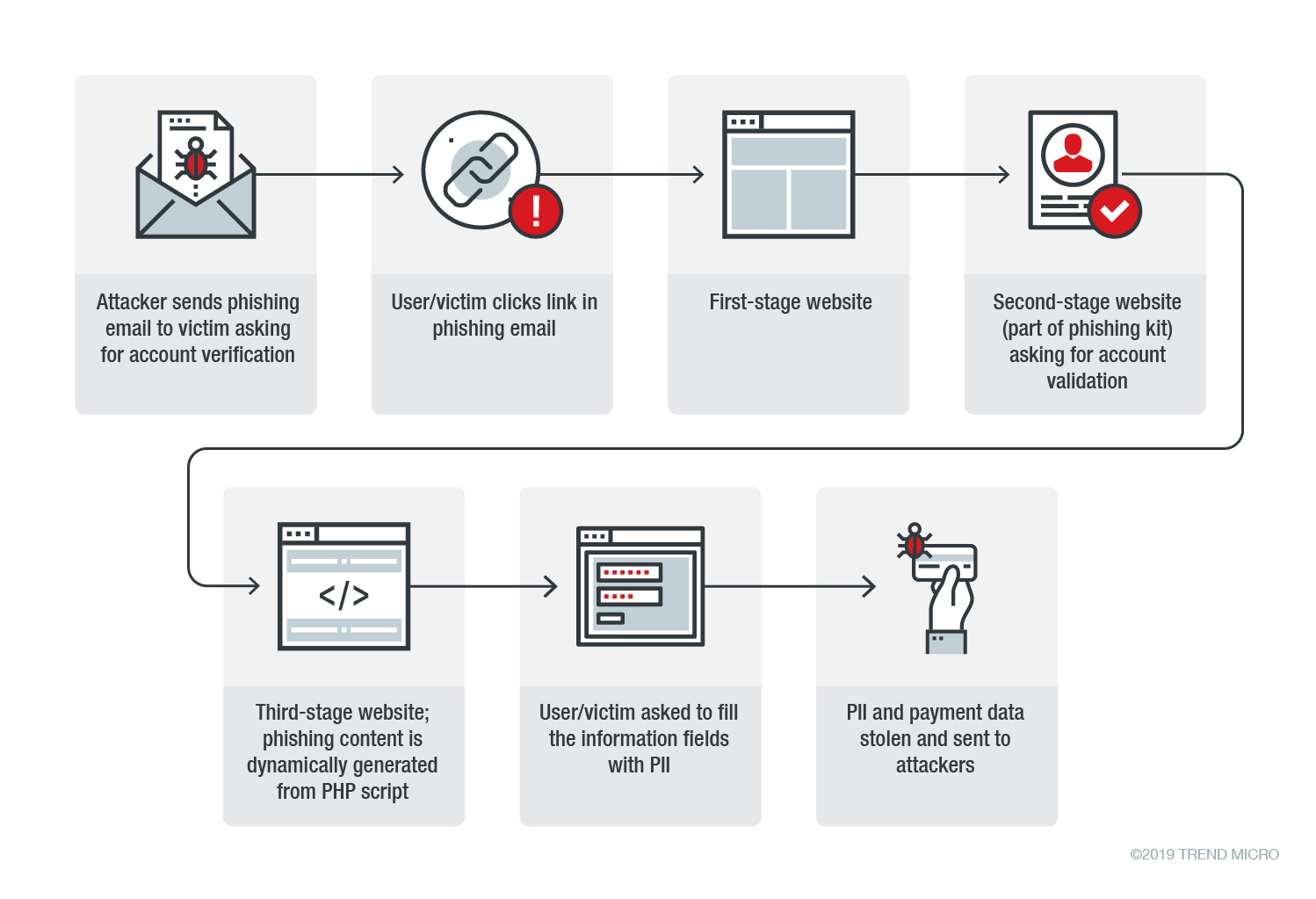
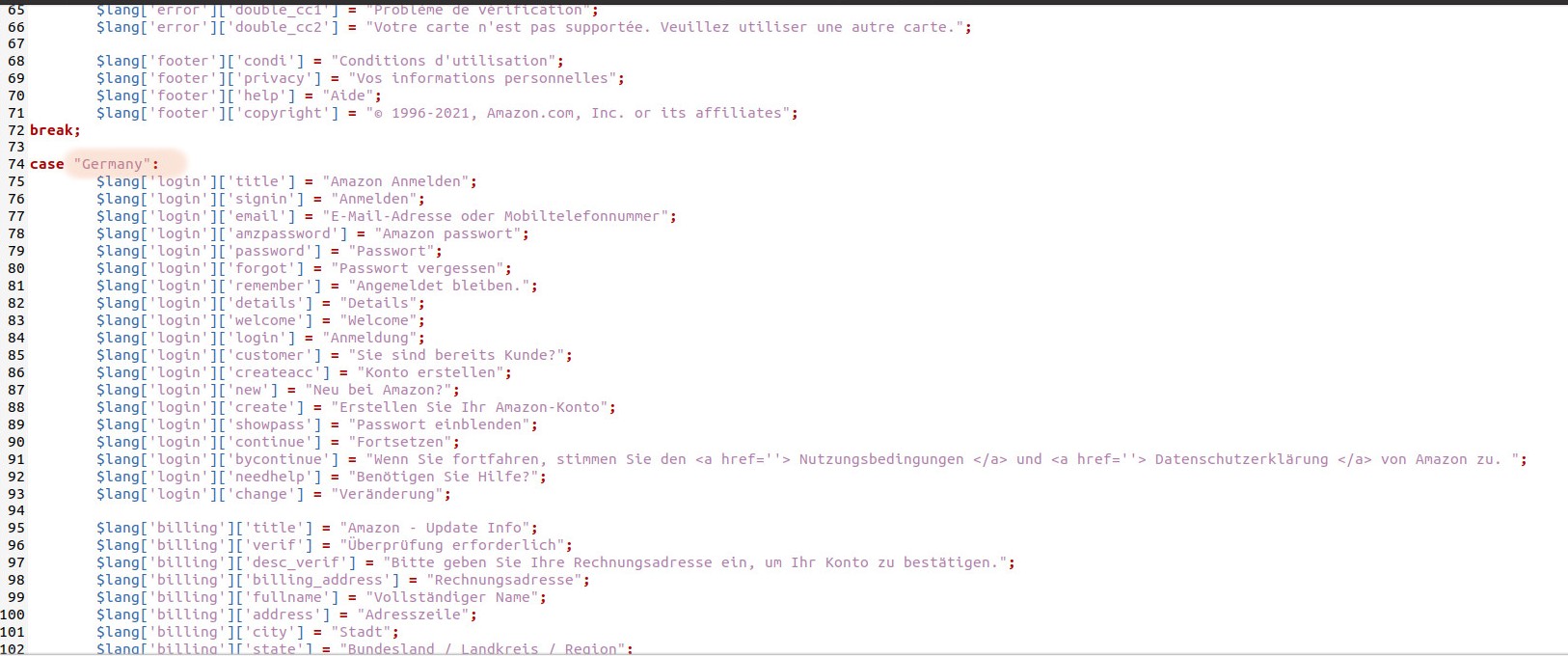
![Phishing kit] Coinbase phishing kit with live admin panel to bypass MFA – an analysis. – StalkPhish – phishing and brand impersonation detection Phishing kit] Coinbase phishing kit with live admin panel to bypass MFA – an analysis. – StalkPhish – phishing and brand impersonation detection](https://stalkphishhome.files.wordpress.com/2023/01/coinbase-mfa-kit_analysis.png?w=1084)
Phishing kit] Coinbase phishing kit with live admin panel to bypass MFA – an analysis. – StalkPhish – phishing and brand impersonation detection

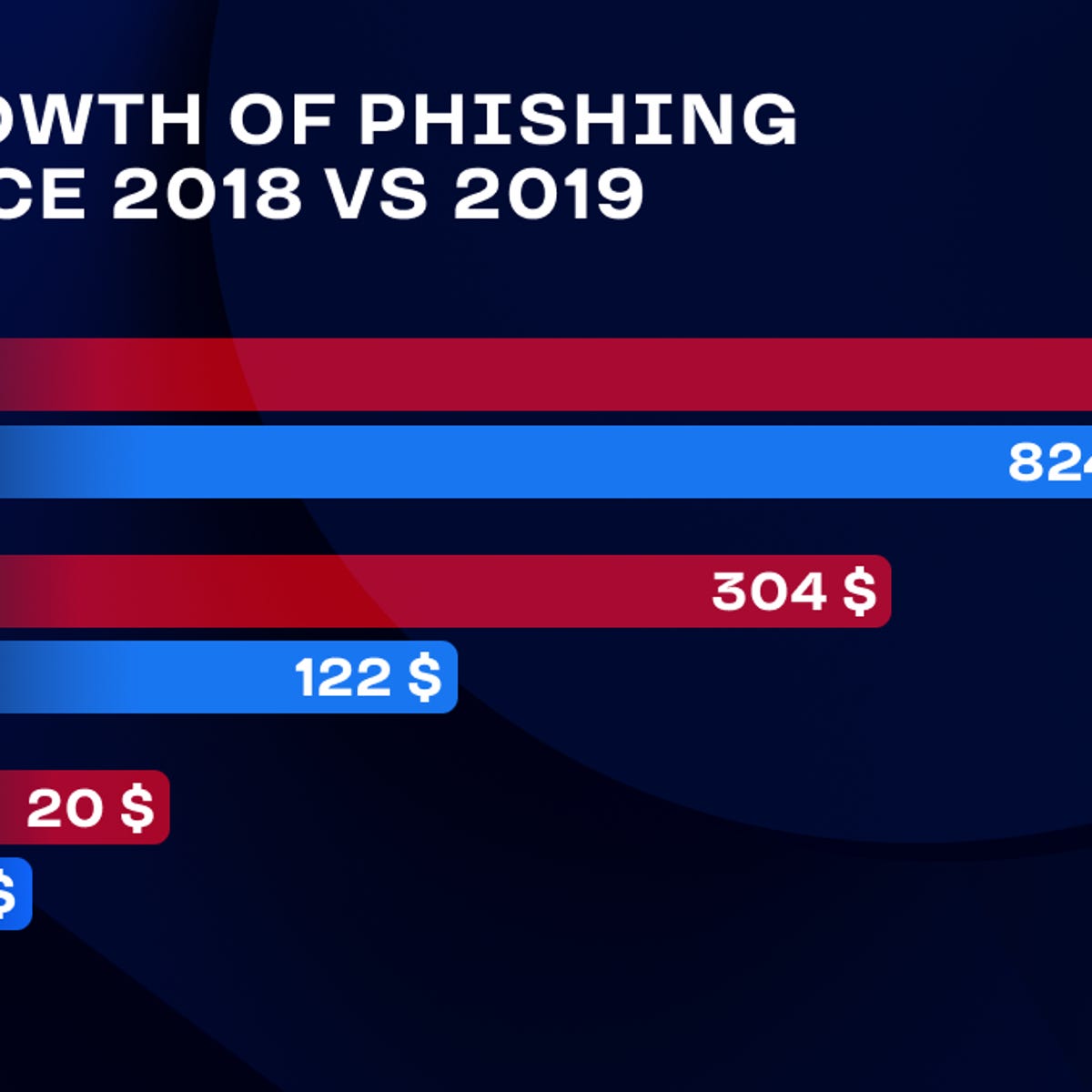
Group-IB: the use of phishing kits surges by 25% in 2022 as they become more evasive and advanced | Group-IB
GitHub - phish-report/IOK: IOK (Indicator Of Kit) is an open source ruleset of phishing threat actor tools and tactics